![]() You’ll find a list and brief description of daemons in Fedora Core 5 at www.mjmwired.net/resources/mjm-services-fc5.html.
You’ll find a list and brief description of daemons in Fedora Core 5 at www.mjmwired.net/resources/mjm-services-fc5.html.
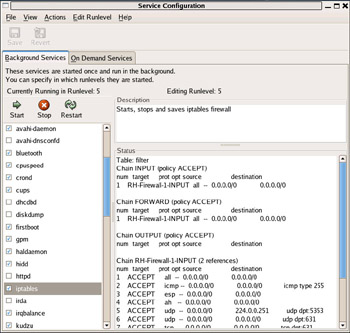
![]() To configure the daemons, navigate to System | Administration | Services. (Fedora actually uses the Windows terminology to refer to the daemons as services.) This will open the GUI interface shown in Figure 14.1.
To configure the daemons, navigate to System | Administration | Services. (Fedora actually uses the Windows terminology to refer to the daemons as services.) This will open the GUI interface shown in Figure 14.1.
![]() Highlighting a service in the leftmost pane will pull up a description and some additional details in the Description and Status panes, respectively. Disabling a service is as easy as removing the check mark next to the service in question, then clicking Save in the upper-right corner of the window and rebooting.
Highlighting a service in the leftmost pane will pull up a description and some additional details in the Description and Status panes, respectively. Disabling a service is as easy as removing the check mark next to the service in question, then clicking Save in the upper-right corner of the window and rebooting.
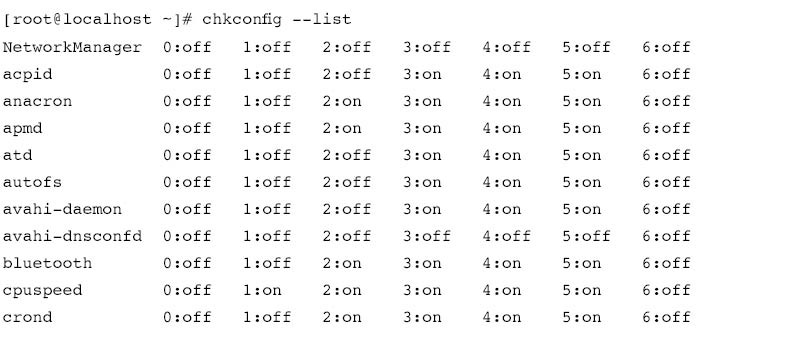
![]() If you are administering the bastion host without access to a GUI front end, you will need to control daemons via the startup scripts. It’s also a good idea to know how to control the daemons without the GUI because the GUI interface will vary from system to system. The methods for startup scripts can also vary from one distribution to another.The startup services in Fedora Core are managed by startup scripts located in /etc/rc.d/init.d. All you need to do is comment out the line that calls the specific script by inserting a # at the front of the line that calls it.You can also edit the individual scripts themselves for control of the way the services are initialized.The preferred way on Fedora Core is to use the chkconfig utility, which can be found in many distributions.You must be logged in as root to use this utility. Abbreviated output from chkconfig --list is shown in Figure 14.2.
If you are administering the bastion host without access to a GUI front end, you will need to control daemons via the startup scripts. It’s also a good idea to know how to control the daemons without the GUI because the GUI interface will vary from system to system. The methods for startup scripts can also vary from one distribution to another.The startup services in Fedora Core are managed by startup scripts located in /etc/rc.d/init.d. All you need to do is comment out the line that calls the specific script by inserting a # at the front of the line that calls it.You can also edit the individual scripts themselves for control of the way the services are initialized.The preferred way on Fedora Core is to use the chkconfig utility, which can be found in many distributions.You must be logged in as root to use this utility. Abbreviated output from chkconfig --list is shown in Figure 14.2.
![]() As you can see, apmd (which is used for monitoring and logging the battery status) is configured to start for run levels two through five. Since our bastion host has no battery to monitor, we can disable apmd for all run levels by entering:
As you can see, apmd (which is used for monitoring and logging the battery status) is configured to start for run levels two through five. Since our bastion host has no battery to monitor, we can disable apmd for all run levels by entering:
 chkconfig --level 123456 apmd off
chkconfig --level 123456 apmd off![]() If you want to remove the service entirely form the startup script, type:
If you want to remove the service entirely form the startup script, type:
 chkconfig –del apmd
chkconfig –del apmd Removing Optional Software
Removing Optional Software
![]() As with Windows, you will also likely end up with some software you don’t need. Removing the software is most easily accomplished with Pirut, the built-in GUI tool you can access by navigating to Applications | Add/Remove Software. Once it finishes checking what is currently installed on the system, you see the Package Manager window, which allows you to search for packages, install packages, or remove them. When you use the Browse button, your interface is hierarchical and looks almost exactly like the one you used to install the operating system.The Package Manager window is shown in Figure 14.3.
As with Windows, you will also likely end up with some software you don’t need. Removing the software is most easily accomplished with Pirut, the built-in GUI tool you can access by navigating to Applications | Add/Remove Software. Once it finishes checking what is currently installed on the system, you see the Package Manager window, which allows you to search for packages, install packages, or remove them. When you use the Browse button, your interface is hierarchical and looks almost exactly like the one you used to install the operating system.The Package Manager window is shown in Figure 14.3.
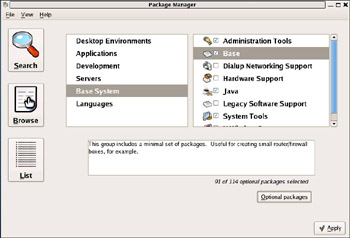
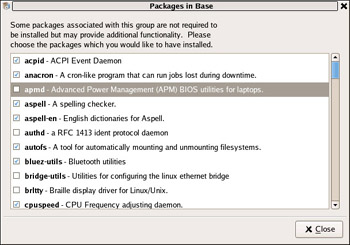
![]() To remove the aforementioned apmd package, highlight the Base System category in the left pane, and then highlight the Base group in the right pane. Click Optional packages and a new window will open showing all packages in the Base group, as shown in Figure 14.4. Simply clear the check mark next to apmd and click Close. Back at the Package Manager window, click Apply. Click Continue on the next window to verify your changes, and finally, click OK when the update is completed.
To remove the aforementioned apmd package, highlight the Base System category in the left pane, and then highlight the Base group in the right pane. Click Optional packages and a new window will open showing all packages in the Base group, as shown in Figure 14.4. Simply clear the check mark next to apmd and click Close. Back at the Package Manager window, click Apply. Click Continue on the next window to verify your changes, and finally, click OK when the update is completed.
![]() Packages can also be managed from the command line using the RPM Package Manager (RPM).You can view a list of all installed packages by entering:
Packages can also be managed from the command line using the RPM Package Manager (RPM).You can view a list of all installed packages by entering:
 rpm –q -a
rpm –q -a![]() For example, to install the apmd package, you would need to first obtain the package file itself (from www.redhat.com/download/mirror.html, for example) or use the RPMs that were included on the installation CDs.Then enter the following command to install apmd:
For example, to install the apmd package, you would need to first obtain the package file itself (from www.redhat.com/download/mirror.html, for example) or use the RPMs that were included on the installation CDs.Then enter the following command to install apmd:
 rpm –i apmd-3.2.2-3.2.i386.rpm
rpm –i apmd-3.2.2-3.2.i386.rpm![]() If the installation is successful, you should see output similar to the following;
If the installation is successful, you should see output similar to the following;
Preparing... ########################################### [100%]
1:apmd-3.2.2-3.2 ########################################### [100%]
![]() You can even install a package directly from the Internet by specifying the full FTP or HTTP path as the path to the RPM, as follows:
You can even install a package directly from the Internet by specifying the full FTP or HTTP path as the path to the RPM, as follows:
 rpm –i ftp://somesite.com/5/i386/RPMS/apmd-3.2.2-3.2.i386.rpm
rpm –i ftp://somesite.com/5/i386/RPMS/apmd-3.2.2-3.2.i386.rpm![]() To uninstall the package, you must use the package name, which can differ from the name of the RPM file.To uninstall apmd, enter the following command, using the –e switch, for erase:
To uninstall the package, you must use the package name, which can differ from the name of the RPM file.To uninstall apmd, enter the following command, using the –e switch, for erase:
 rpm –e apmd-3.2.2-3.2
rpm –e apmd-3.2.2-3.2| Tip |
|
pup GUI tool for updating software, accessed at Applications | System Tools | Software Updater.
pirut GUI tool for managing software packages, accessed at Applications | Add/Remove Software.
rpm Command-line tool for managing software packages.
yum Yellowdog updater modified; command-line tool for managing software packages.
yum Extender A GUI interface for YUM (install with yum install yumex).
Pirut and yum will automatically ensure you have the most current version of a package. Both of these will also automatically check and install any dependencies for the software you install. Rpm does not include this functionality; you will need to check for dependencies manually when using rpm. YUM only works on RPM based systems, and not all systems will have YUM available/installed, therefore it is suggested that you understand how to manage packages with RPM even if you choose to use YUM for you day to day management.
![]() There is no universal list to tell you which packages you should leave installed and which ones you should remove.You will need to evaluate each service based on your requirements. However, at a minimum the following services are ones you probably do need to have installed/running, unless you are very sure you don’t need them:
There is no universal list to tell you which packages you should leave installed and which ones you should remove.You will need to evaluate each service based on your requirements. However, at a minimum the following services are ones you probably do need to have installed/running, unless you are very sure you don’t need them:
-
 haldaemon Used for gathering and maintaining information concerning hardware devices
haldaemon Used for gathering and maintaining information concerning hardware devices -
 iptables Manages IPTables firewalls
iptables Manages IPTables firewalls -
 messagebus Used for sending notification for certain system events
messagebus Used for sending notification for certain system events -
 network Manages the activation of network interface at boot-up
network Manages the activation of network interface at boot-up -
 NTPd Used to synchronize time via the NTP protocol
NTPd Used to synchronize time via the NTP protocol -
 sshd Runs OpenSSH server
sshd Runs OpenSSH server -
 syslogd Used for system logging
syslogd Used for system logging -
 xinetd Manages the startup of services
xinetd Manages the startup of services
![]() There are some services that you would never want exposed to an untrusted network such as the Internet. In most cases this means they should not be running on a bastion host. These services include the following:
There are some services that you would never want exposed to an untrusted network such as the Internet. In most cases this means they should not be running on a bastion host. These services include the following:
-
 portmap Used to manage RPC connections
portmap Used to manage RPC connections -
 Telnet Used for unencrypted remote console access
Telnet Used for unencrypted remote console access -
 rsh, rlogin, rexec Used for unencrypted remote console access
rsh, rlogin, rexec Used for unencrypted remote console access -
 nfs, lockd, mountd, statd Used for Network File System (NFS) and related services
nfs, lockd, mountd, statd Used for Network File System (NFS) and related services -
 lpd Printer service
lpd Printer service

0 comments
Post a Comment